The SharePoint Hack Proves Admin-Level Permissions Are a Cybersecurity Time Bomb

Table of contents
In July 2025, Microsoft announced that Chinese hackers had breached a slew of on-premises SharePoint servers, commandeering the sensitive data, trade secrets, and intellectual property hosted there.
The whole episode exposed a common yet often-overlooked cybersecurity weakness: granting third-party applications excessive privileges.
Specifically, it highlighted the risks organizations face when apps require application-level permissions to Microsoft SharePoint, creating a high-risk entry point for attackers.
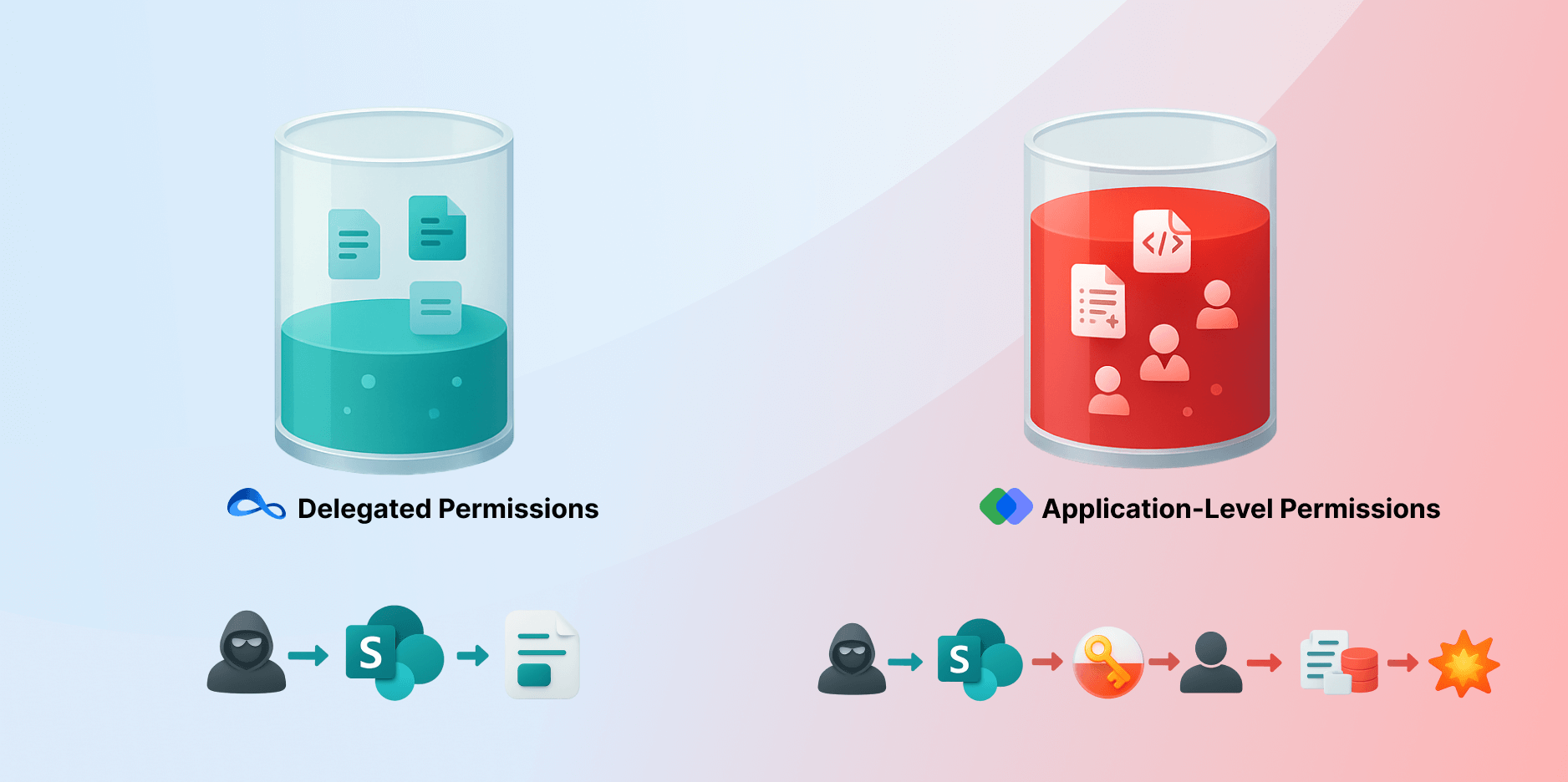
In today’s sophisticated threat landscape — where every access point is a potential vulnerability — granting application-level permissions to third-party applications is dangerous and can put an organization’s data security at risk.
Example: Connecting Microsoft Teams and Google Workspace
If your organization uses both Microsoft Teams and Google Workspace — and you want to connect the two services to increase productivity, reduce context switching, and otherwise improve your security posture — there are two solutions you can turn to:
- NextPlane OpenHub
- Mio
While there are several key differences between these two options, the SharePoint hack highlights another key differentiator. To enable interoperability between Teams and Google Workspace, Mio requires super admin application-level permissions — such as Files.ReadWrite.all and Group.ReadWrite.All — while NextPlane OpenHub only requires delegated-level permissions.
What’s the difference? Application permissions are used by apps that run without signed-in users; the app itself is trusted and given permissions directly. Delegated permissions, on the other hand, are used by apps that act on behalf of signed-in users; here, the app can do whatever the user is allowed to do.
While Mio’s application-level permissions requirement may make it more convenient for their interoperability solution, it can become a serious trap for customers — something made crystal clear by the SharePoint hack.
When you deploy an interop solution, you’re ostensibly trying to make life easier for your employees. But if you’re using a solution like Mio that requires excessive privileges, you are opening the backdoor to bad actors, who can then access your organization’s SharePoint files, where they can exploit Files.ReadWrite.All, which allows apps to create, update, and delete all files that live in your organization’s SharePoint libraries and OneDrive accounts, and Group.ReadWrite.All, which enables apps to create, update, and delete groups that live in your organization’s directory.
In other words: unnecessary application-level privileges can enable hackers to modify, steal, or even delete every single file on your organization’s SharePoint — including source code, financial statements, intellectual property, and sensitive customer information. They can also create and delete users and groups, which can significantly hinder organizational productivity.
Compare that to organizations using NextPlane OpenHub to connect Teams and Google Workspace. During a SharePoint breach, hackers wouldn’t have access to the organization’s SharePoint server or any of the files that are shared between Google Workspace and Teams.
Suffice it to say that’s a lot of effort for a payoff that doesn’t really amount to much.
Just because Microsoft patched the SharePoint vulnerability doesn’t mean Mio customers are in the clear, either.
If hackers target an organization that uses Mio to connect Teams and Google Workspace, they may decide to penetrate the Mio Interoperability solution directly, gaining access to the organization’s SharePoint and all of its contents due to the Files.ReadWrite.All application-level permissions Mio requires.
Evaluate the security posture of every tool in your tech stack
When it comes to assembling your tech stack, it’s critical to consider the level of permissions each integration between tools requires. While two solutions may look similar on the surface, there can be drastic differences under the hood that could wreak havoc on your operations if overlooked.
The last thing an IT manager wants is for a CTO to call them after learning that sensitive operational data was stolen due to excess permissions — something that’s entirely avoidable. Depending on how bad the breach is, errors and omissions insurance can only do so much — especially when customers and regulators start asking questions.
Prevention is always cheaper than cleanup. By choosing tools and integrations that adhere to the principle of least privilege, you can rest comfortably knowing that your stack is full of applications that only require the minimum access necessary to function.
In an era of increasingly sophisticated cyberattacks — all of which are becoming more common with each passing day — every level of permission you grant is either a safeguard or a liability. So choose wisely and keep your most sensitive data safe.
Learn more about why NextPlane OpenHub is the most secure interop solution for Microsoft Teams and Google Workspace.





